File servers are high-powered computers that enable data sharing for a network of users, devices, and clients.
One of the earliest uses of servers was for the simple storage and management of data on an on-premises network. File servers are a central database for the network where permitted devices can access files hosted by the file server, save progress after editing, and ensure the file remains secure beyond their local storage.
This article looks at what a file server is, how it provides resources to a network, and what file servers look like in modern applications.
What Is A File Server?
A file server is a type of server responsible for the storage, access, and management of data files for a network of devices. Before file servers, users could save data files to their local hard drive or use a mobile storage unit — like a floppy disk or a USB stick. This presents two issues:
- Sensitive data stored in a single location is at risk of misplacement, theft, or ruin
- Exchanging files within organizations is difficult when limited to isolated systems
File servers resolve both of these roadblocks by offering a central repository of network data accessible to users, also known as clients.
Why Do I Need A File Server?
Today, with a growing number of devices designed for on-the-go use, file server capabilities still play a critical role in securing files intended for a collective group of users. What’s changed is the multitude of on-premises appliances, software, and cloud systems that now fulfill the role of a file server.
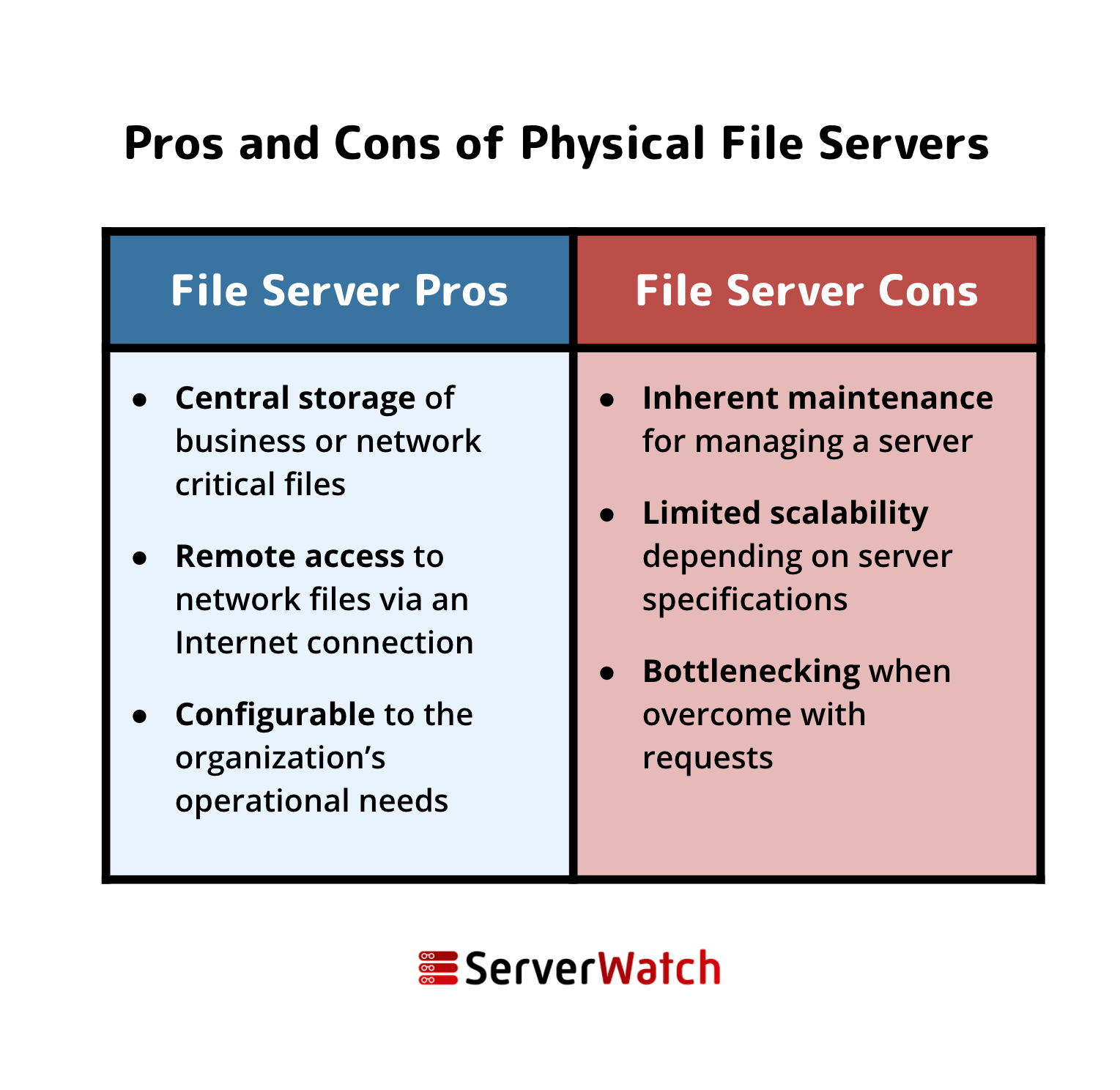
It’s worth noting that the file server cons above apply more to the traditional perception of a file server in its physical appliance form. In the past, having a file server meant all of the responsibilities of managing a server. Today’s cloud-based solutions make file serving reasonably convenient.
Learn more about the top distributed? network resources on the market in our Best Load Balancers of 2021.
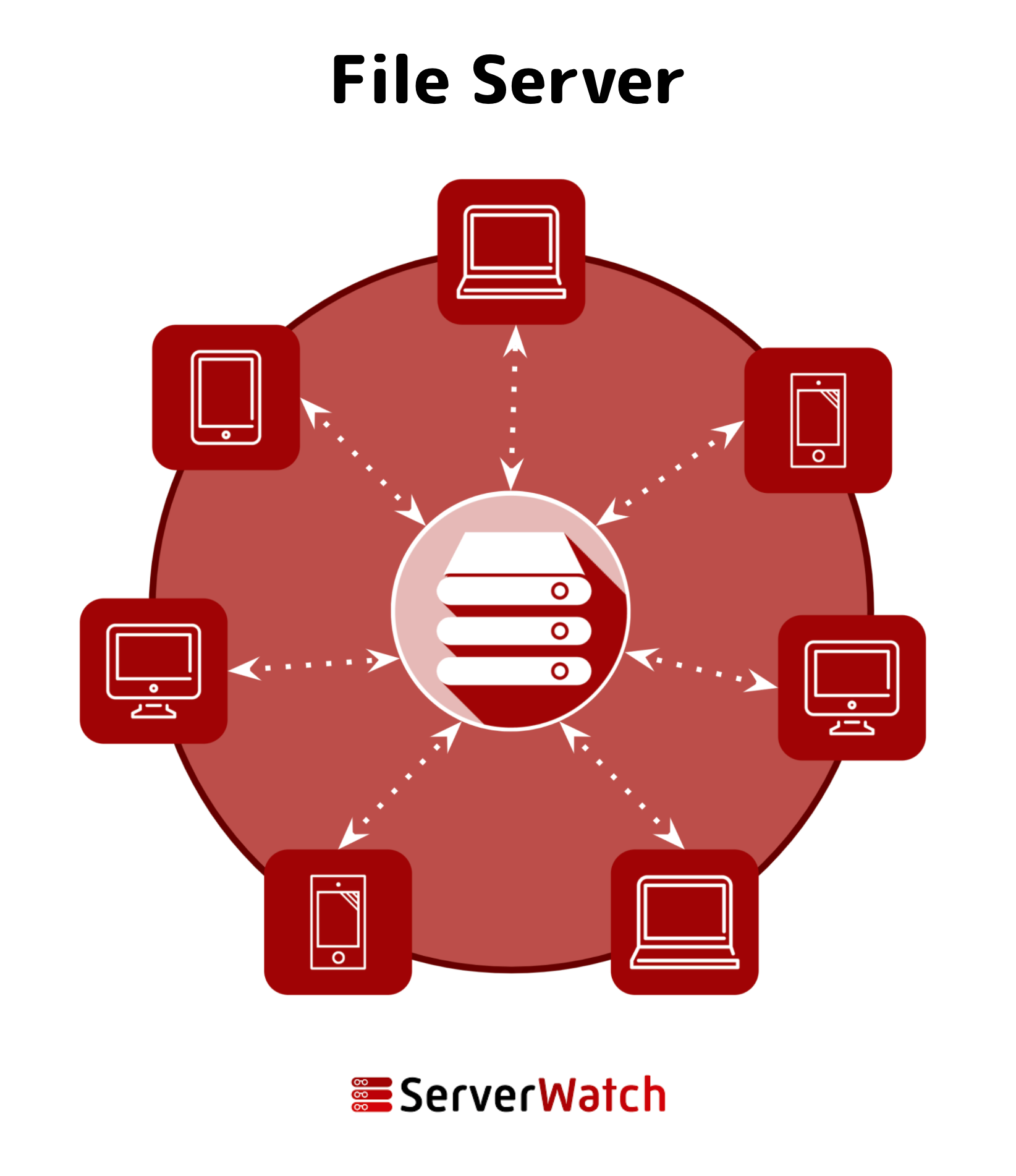
How Do File Servers Work?
The above graphic shows how file servers work in a nutshell. At the back end of an office or a network’s data center, a file server devotes its operations to creating, storing, editing, and transferring files for use by client devices.
Similarly, cloud-based storage solutions like Box and Microsoft SharePoint have their own data centers devoted to hosting file servers for web users.
File Servers in the Age of Cloud Computing
As file serving is a critical part of any operating network, one of the first offerings cloud service providers released was storage and file transfer solutions. Unlike their physical predecessors, cloud-based storage solutions are more scalable, cost-efficient, and easier to maintain.
As on-premises infrastructure remains a critical component of a developed network, cloud service providers offer hybrid file storage. Both on-prem appliances and cloud services work in conjunction to maximize security and access.
Popular Cloud File Server Solutions
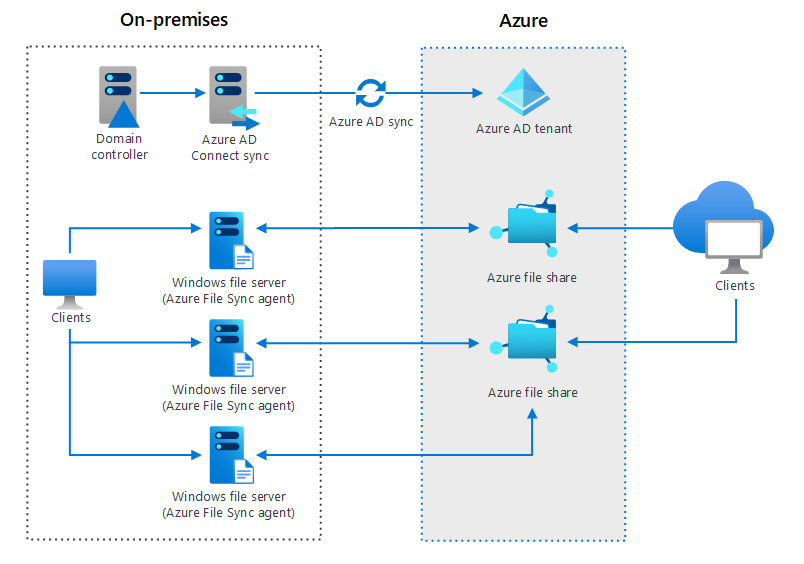
Hybrid File Servers
One example of a hybrid file storage and sharing system is the Azure architecture, as seen in the graphic above. Between existing on-premises Windows file servers and the organization’s Azure Active Directory tenant, both staff and external clients can use an ecosystem of file sharing that updates simultaneously.
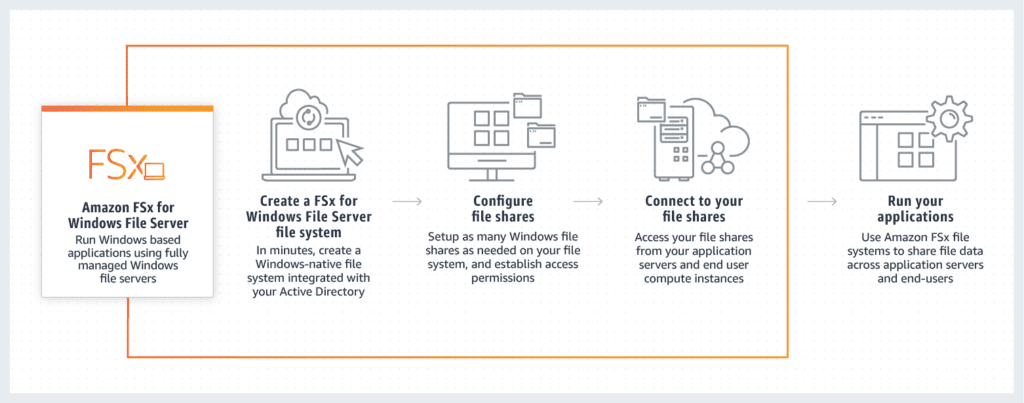
Amazon Web Services (AWS) offers a few options for cloud file serving, but the above graphic highlights their online file server dubbed the Amazon FSx, which is designed to work for Windows-based systems. The visual touches on how clients can quickly get started by signing up, setting configurations, and establishing the flow between on-premises and cloud storage spaces.
From Local to Network-Level Vulnerability
Because file servers are one of the oldest network appliances, IT veterans know all too well how they present risks to data. While cybersecurity has become more complex, a file server for an organization is an excellent example of how a purposeful and worthy solution can also present inherent vulnerabilities. Whereas before, a sensitive file might only be accessible to one or two people, now a network of users might have access.
Unauthorized access and insider threats are the most significant risks to server cybersecurity when deploying a file server.
Want to learn more about vulnerabilities presented by cloud storage? Read eSecurityPlanet’s Guide to Cloud Bucket Vulnerability Management in 2021.
Featured Partners: Vulnerability Management Software
NinjaOne
NinjaOne helps IT teams identify and remediate vulnerabilities via endpoint monitoring, patch management, and device configuration hardening. Quickly identify device and application misconfigurations and implement corrective actions at scale via custom policies or scripts.
• Automatic prioritization of mitigation actions
• Reduce patching time by up to 90%
• Leverage cloud-first backup options to defend against ransomware
Purple Knight
With Purple Knight's Active Directory security audit, spot threats before attackers do. Purple Knight scans your AD, Azure AD, and Okta to find risky configurations and security vulnerabilities. See your security audit scores in minutes, and get prescriptive guidance from identity security experts to help you prioritize remediation efforts.
ESET PROTECT Complete
ESET PROTECT Complete adds extra protection to your Microsoft 365 cloud email, collaboration & storage or mail servers. This solution includes advanced threat defense technology, preventing new, never-before-seen threats through cloud sandboxing, vulnerability & patch management to reduce your attack surface and full disk encryption capability for enhanced data protection. It’s completely manageable through the ESET PROTECT Cloud console improving total cost of ownership. Limited time: 20% Off.
AppTrana
AppTrana is a fully managed WAF that provides real-time protection against DDoS attacks, bot threats, and application vulnerabilities. It ensures zero false positives on all managed security policies, minimizing disruptions to legitimate traffic. With zero-day protection backed by a 24-hour SLA and rapid onboarding in just 5 minutes, AppTrana delivers continuous monitoring, automated threat mitigation, and 24/7 expert support to safeguard applications from evolving cyber threats.
SanerNow Vulnerability Management Tool
Saner Vulnerability Management Tool is an all-in-one, continuous, and automated solution.
At one glance, here's what you need to know: The world's largest vulnerability database with 190,000+ checks, rapid scans within 5 minutes, and 99.99% accuracy.
Saner Continuous Vulnerability and Exposure Management (CVEM) platform, integrates with vulnerability and patch management to detect and remediate vulnerabilities beyond CVEs and exposures, all in a single console.






